
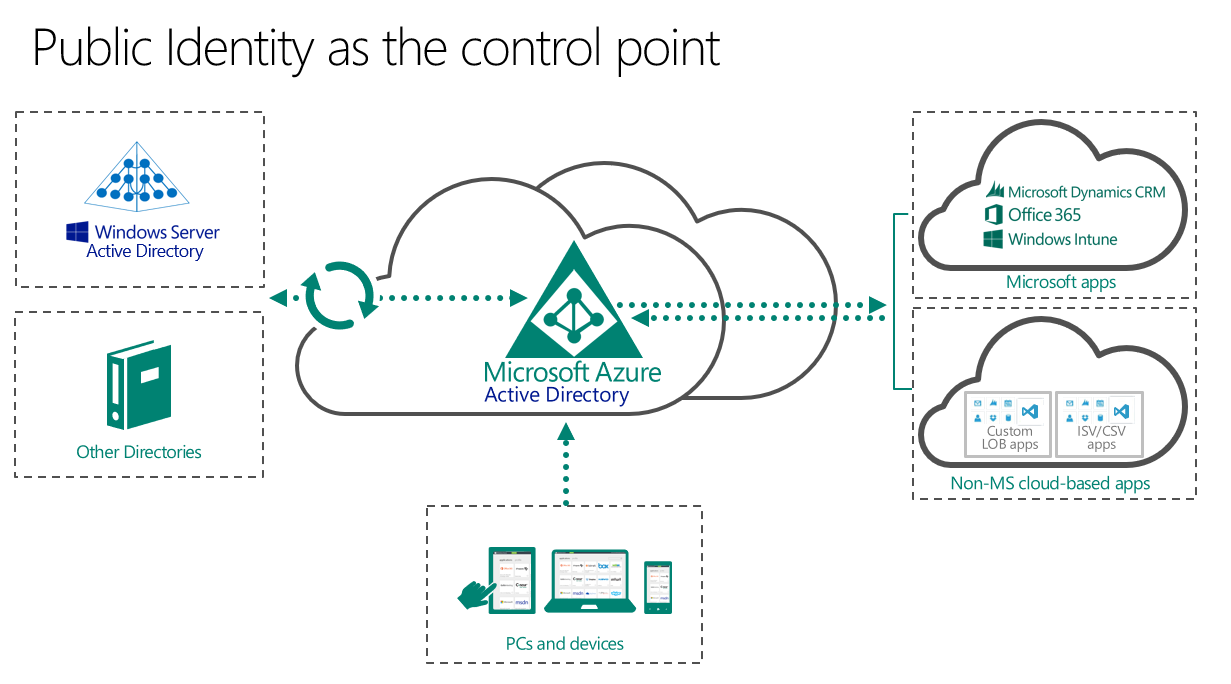
Enterprise Mobility + Security (EMS) is a cloud-based offering from Microsoft which combines valuable standalone solutions in a highly discounted suite, licensed on a per user base. EMS integrates Identity and Access Management, Mobile Application (MAM) and Mobile Device Management (MDM) solutions with security solutions for information protection and threat management.
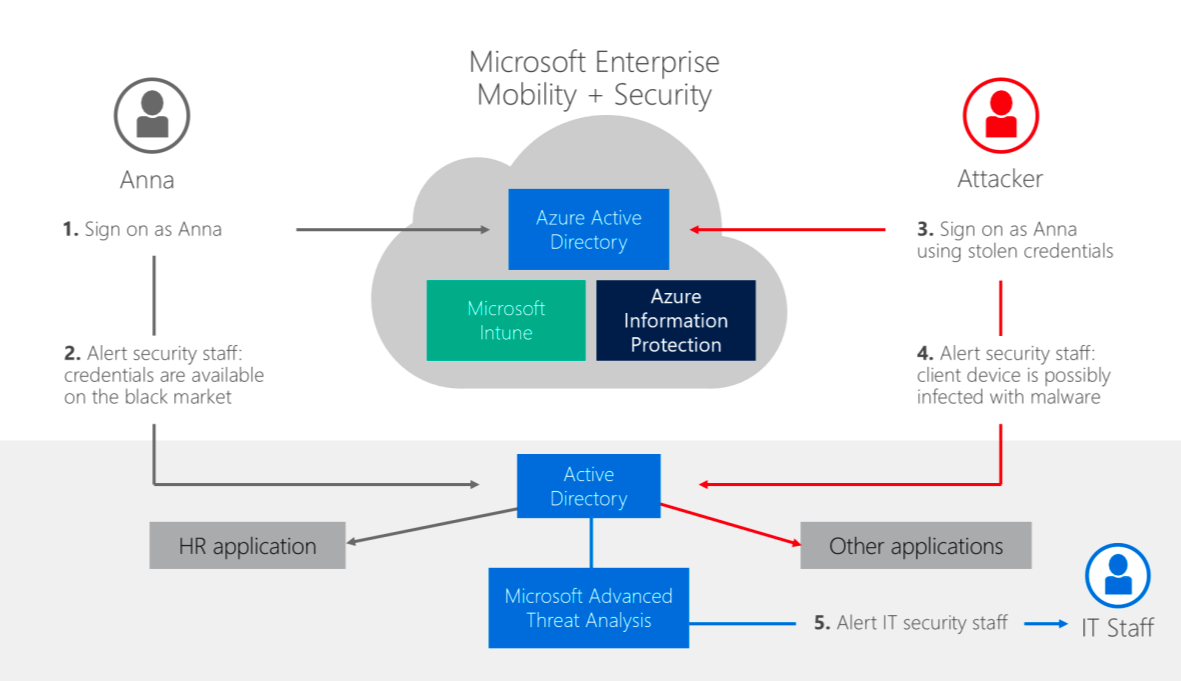
EM+S is made up of five different products: Azure Active Directory, Microsoft Intune, Azure Information Protection, Microsoft Advanced Threat Analytics, and Microsoft Cloud App Security*. These five products allow you to have complete security and control of your data and devices.
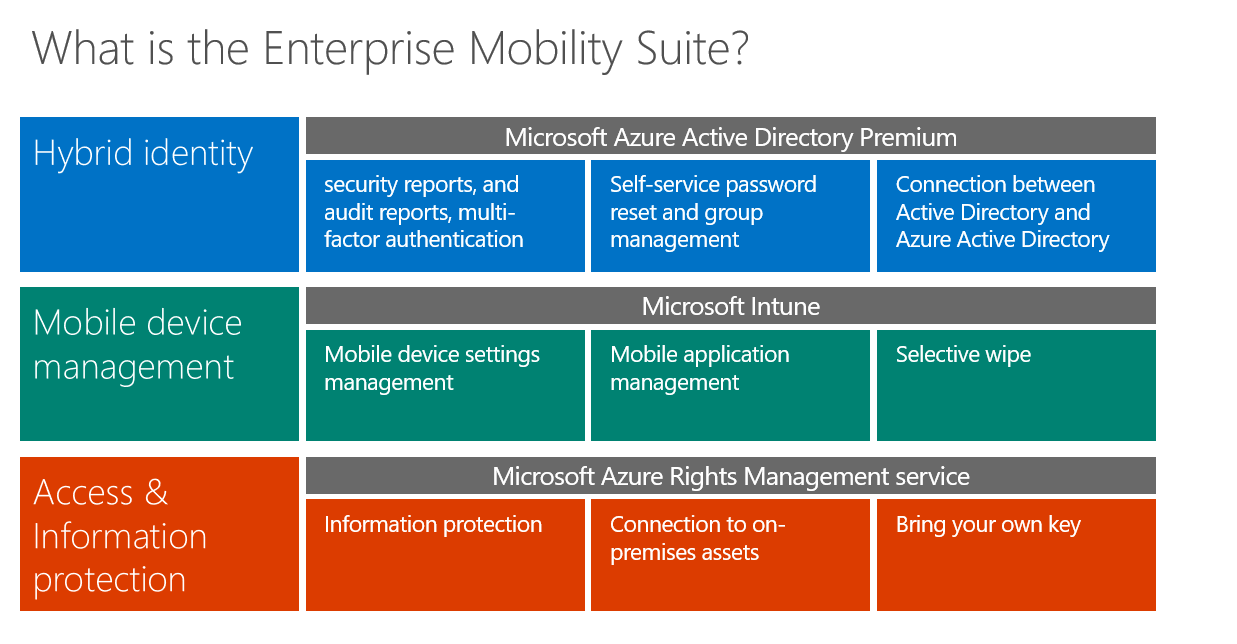
In a modern work-space where mobility and Bring-your-own-device (BYOD) scenarios gain increasing significance, Enterprise Mobility + Security can help IT administrators meet the challenges that exist between the best possible user experience and productivity and a high level of security, data protection and risk management.
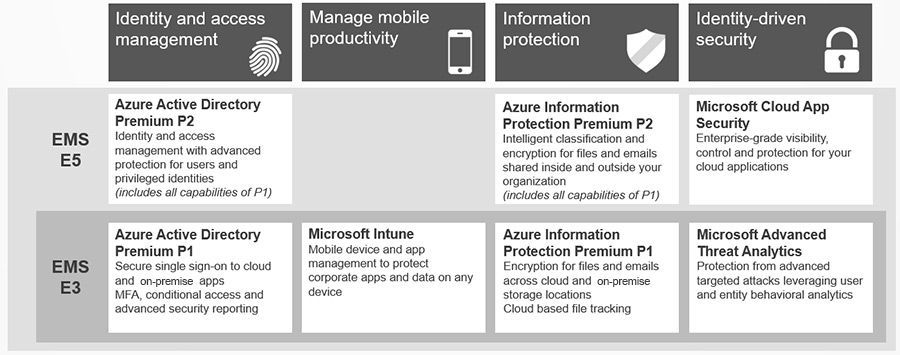
Azure Active Directory Premium:
An increasing number of employees wants to bring their personal devices to work and readily adopts available SaaS applications. This has become a significant challenge for IT departments who need to maintain control over the applications used by employees across corporate datacenters and public cloud platforms. To meet these challenges, Azure Active Directory Premium offers:
- Self-service password reset to reduce helpdesk calls
- Multi-factor authentication options for greater security
- Group-based provisioning and single sign-on for thousands of SaaS apps
- Machine learning-driven security reports for visibility and threat management
- Robust sync capabilities across cloud and on-premises directories
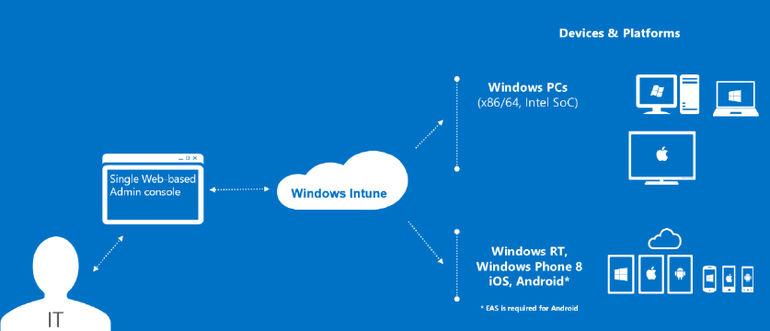
Microsoft Intune:
Mobile devices become increasing popular in the workplace, as employees want to be able to do their work from virtually anywhere. To remain productive, the mobile workforce demands consistent access to corporate resources and data from any location on any device. The Bring-your-own-device (BYOD) trend has introduced significant challenges for IT administrators who want to enable enterprise mobility while ensuring that corporate resources are protected from unauthorized access. To meet these challenges, Microsoft Intune offers:
- Mobile application management across devices
- Broad device support for iOS, Android, Windows and Windows Phone devices
- Selective wipe of apps and data for greater security
- Use of System Center Configuration Manager and Endpoint Protection
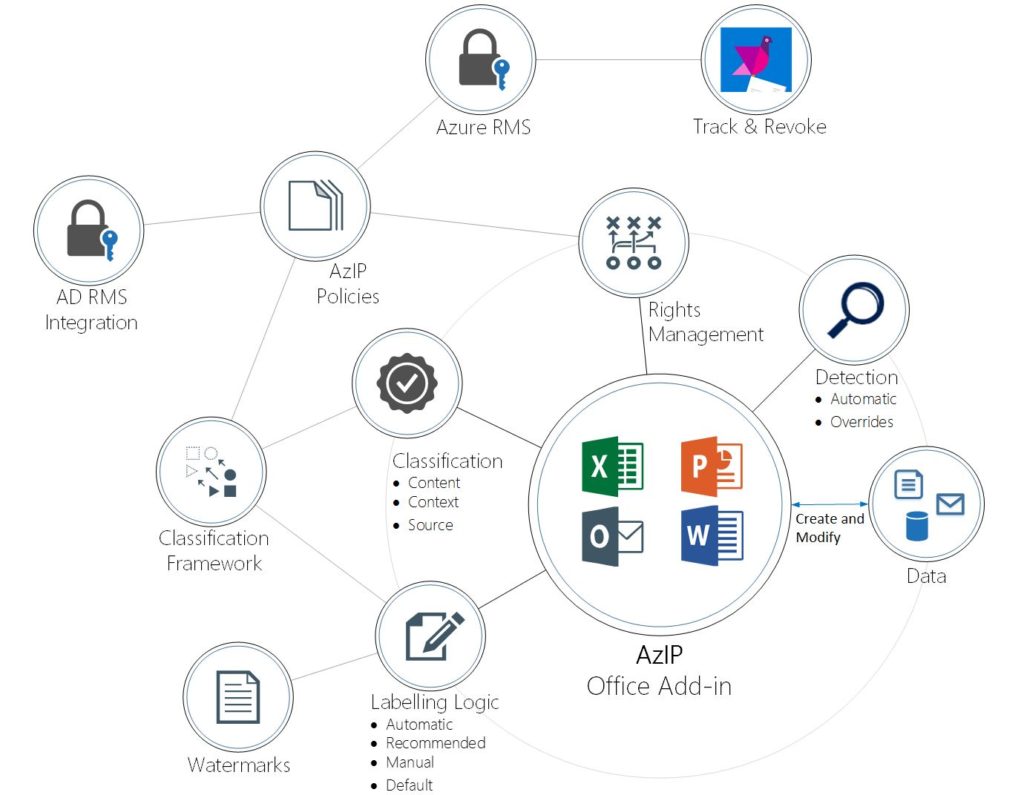
Azure Information Protection
The way that corporate resources are accessed is changing constantly. Users need consistent access to corporate resources from their devices in order to be productive. The need for more secure collaboration with colleagues inside and outside of organizations is also increasing. To meet these challenges Azure Rights Management offers:
- Classification and labeling: Classify data based on sensitivity and add labels—manually or automatically.
- Encryption and rights management: Encrypt your sensitive data and define usage rights when needed.
- Intuitive, one-click process: Apply protection easily without interrupting your employees normal course of work.
- Detailed tracking and reporting: See what’s happening with your shared data to gain more control over it.
- Deployment and management flexibility: Help protect your data whether it’s stored in the cloud or in on-premises infrastructures. You have the flexibility to choose how your encryption keys are managed, including Bring Your Own Key (BYOK) options.
Advanced Threat Analytics
The topic of cyber-security has moved from IT and the datacenter to the highest levels of the boardroom. Attacks and threats have grown substantially more sophisticated in frequency and severity. Everything from customer privacy to brand identity, executive’s reputations and beyond can be at stake. Without a strong defense system in place, the identities and bank accounts of individuals can be hacked, businesses stand to lose customers, and companies can lose control of trade secrets, intellectual property or their competitive edge. To meet these challenges, Advanced Threat Analytics offers:
- Behavioral analytics for advanced threat detection
- Detection for known malicious attacks and security issues
- Simple, actionable feed for the suspicious activity alerts and the recommendations
- Integration with your existing Security Information and Event Management (SIEM) systems
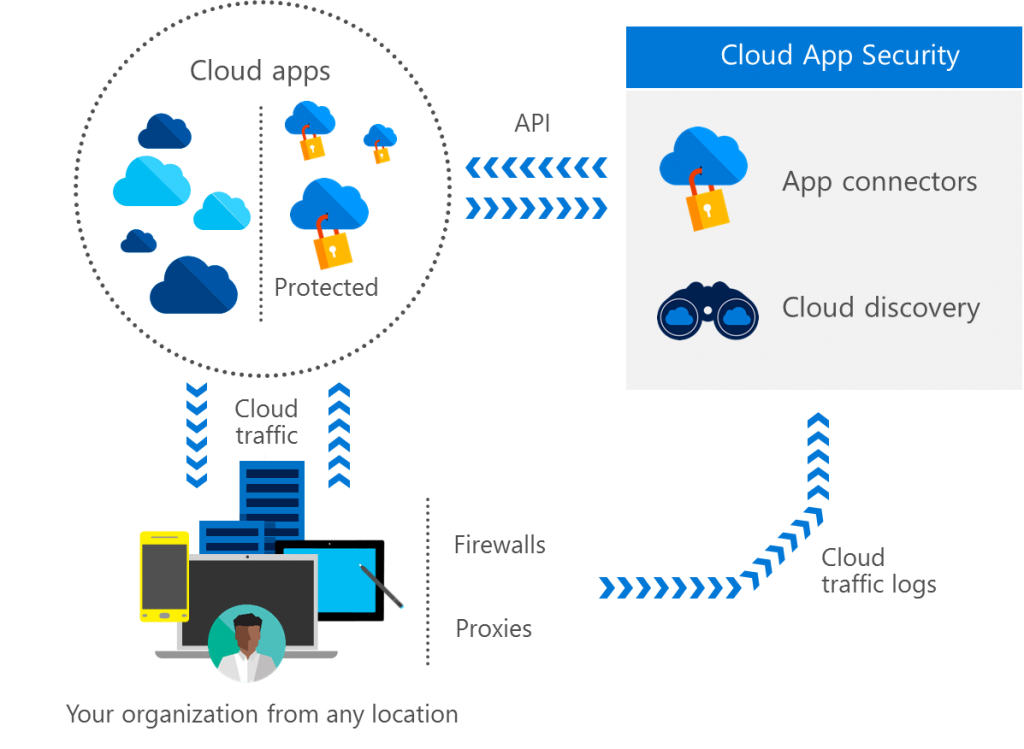
Microsoft Cloud App Security *
Bring the security of your on-premises systems to your cloud applications—both approved and unapproved—for deeper visibility, comprehensive controls, and enhanced protection.
Discovery
It all starts with discovery. Cloud App Security identifies all cloud applications in your network—from all devices—and provides risk scoring and ongoing risk assessment and analytics. No agents required: information is collected from your firewalls and proxies to give you complete visibility and context for cloud usage and shadow IT.
Data Control
Approving an application to be used is not enough. With special focus on sanctioned apps, you can set granular controls and policies for data sharing and DLP. You shape your cloud environment using out-of-the box and custom policies.
Threat Protection
Cloud App Security provides threat protection for your cloud applications that’s enhanced with vast Microsoft threat intelligence and research. Identify high-risk usage, security incidents, and detect abnormal user behavior to prevent threats.
* only available in EMS E5



Leave a Reply